Unleash the Buzz: Active Directory Cicada Enum Tool for Effortless Exploration!
https://github.com/TheBlxckCicada/Cicada-Scan
If you are participating in a red teaming engagement, such as a Pentest, or attempting to enumerate and compromise an AD lab like the ones found in hackthebox , tryhackme, or vulnlab, wouldn't it be helpful to have a tool that could perform basic enumeration tasks for you? This way, you could focus on more significant tasks while the tool handles the routine work.
Red teaming or Pentesting is a process where an ethical hacker is hired to test a company's network by simulating an adversary attempting to steal the company's valuable data or sensitive information. After the testing, the pentester creates a report on their findings and presents it to the company's executives and technical staff. The report contains the details of how the engagement went and highlights the problems or vulnerabilities that the hacker could exploit. Finally, the report suggests how the company can fix these vulnerabilities and improve its security posture.
Even though many pen-testers have checklists to follow, it is essential to conduct basic enumeration to comprehend the active directory layout of the company. This includes understanding how usernames are constructed, the number of registered users in the active directory, and identifying keberoastable users.
The Cicada Scan tool is designed to enumerate Active Directory by focusing on the following tasks: obtaining a list of shared drives and downloading their contents, checking if a user has permission to gain an evil-winrm shell, attempting to retrieve a list of all users in the active directory and testing if they are kerberoastable. Additionally, the tool runs Bloodhound and LDAP. All the results are saved in a structured directory, which makes it easy to locate the desired information. The below show a directory tree on what to expect
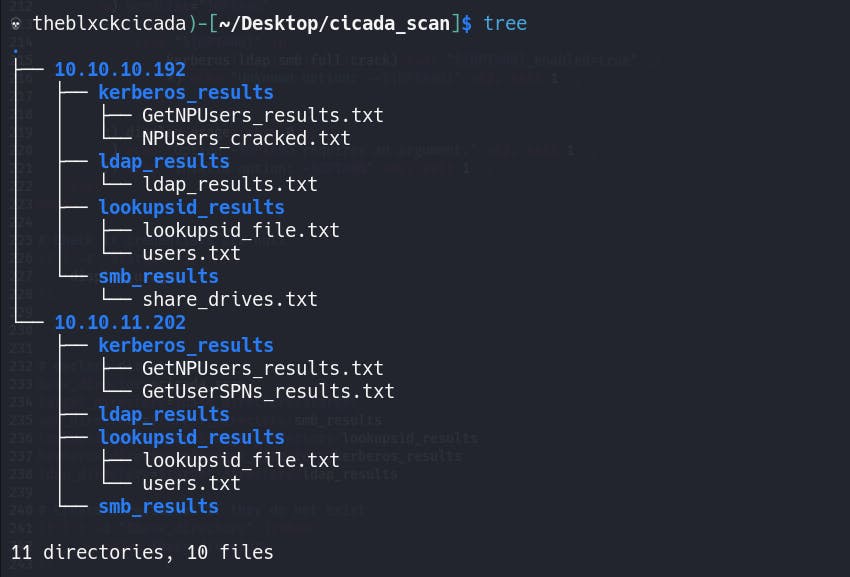
Although I cannot demonstrate all the possible ways to use this tool, I can provide you with a basic guide to get started. If you do not have login credentials yet, don't worry, this tool can attempt to connect with guest and empty credentials. You can also customize what you want to enumerate and what you do not want to enumerate. It is a fun tool to use.
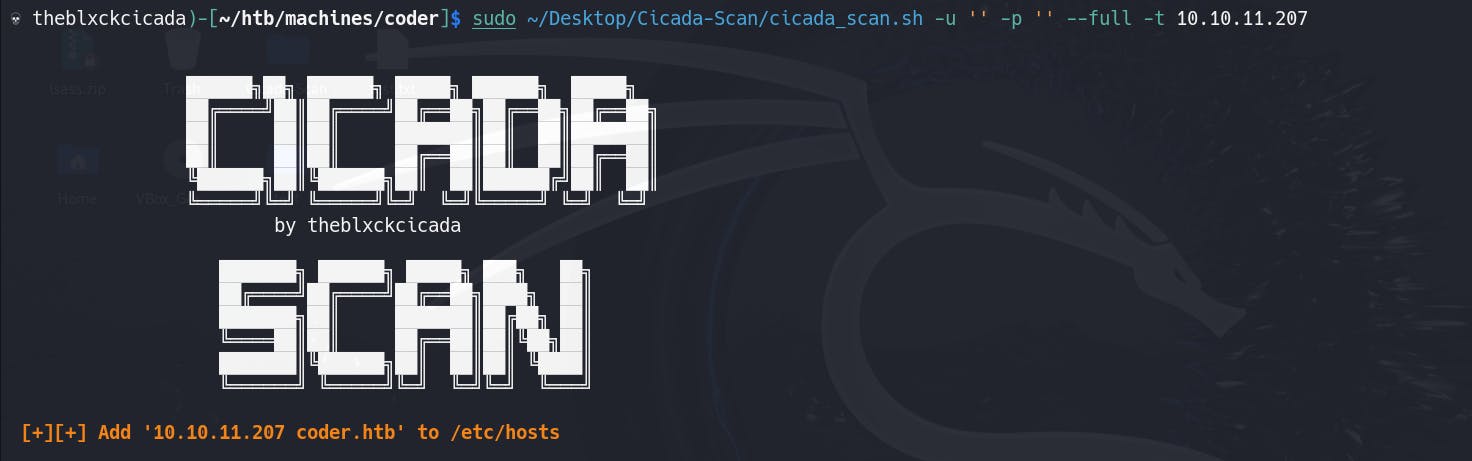
When running the tool against your target for the first time, if you're unsure of the machine's domain, the tool will inform you of the correct domain to add to your host file. Please check the information below for details.
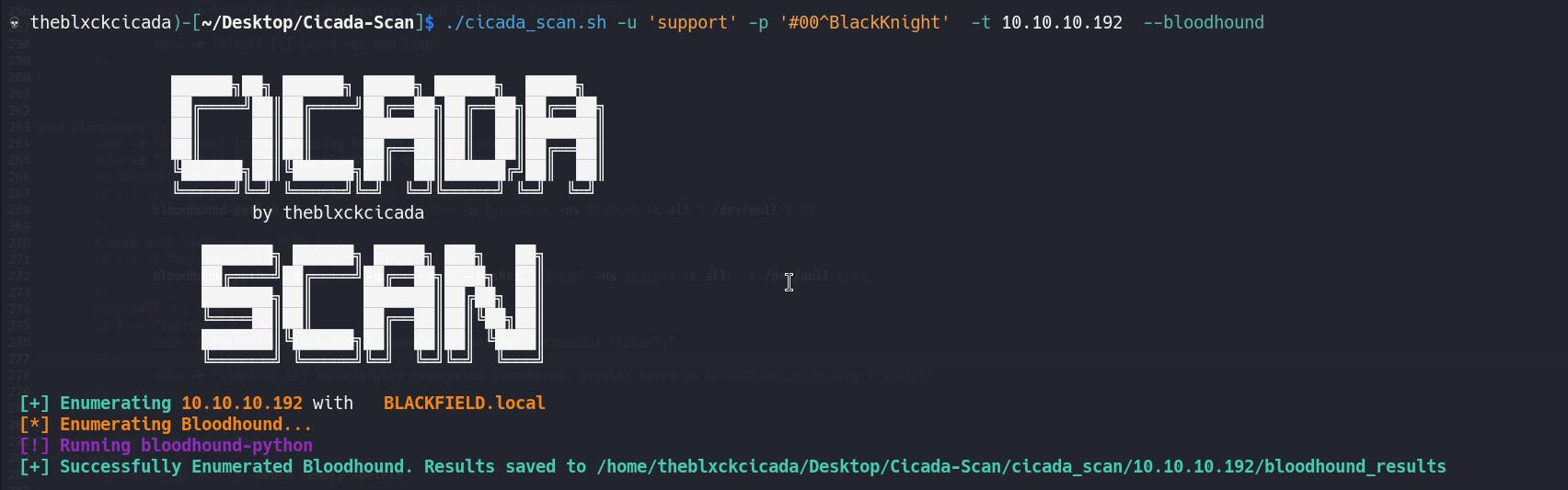
Suppose you have a username and password, but you're only interested in obtaining the Bloodhound files. You don't need to remember the exact command to get them. Instead, you can just specify what you want to enumerate when you run the tool. It will do exactly as you ask because it is attentive and listens to your commands.
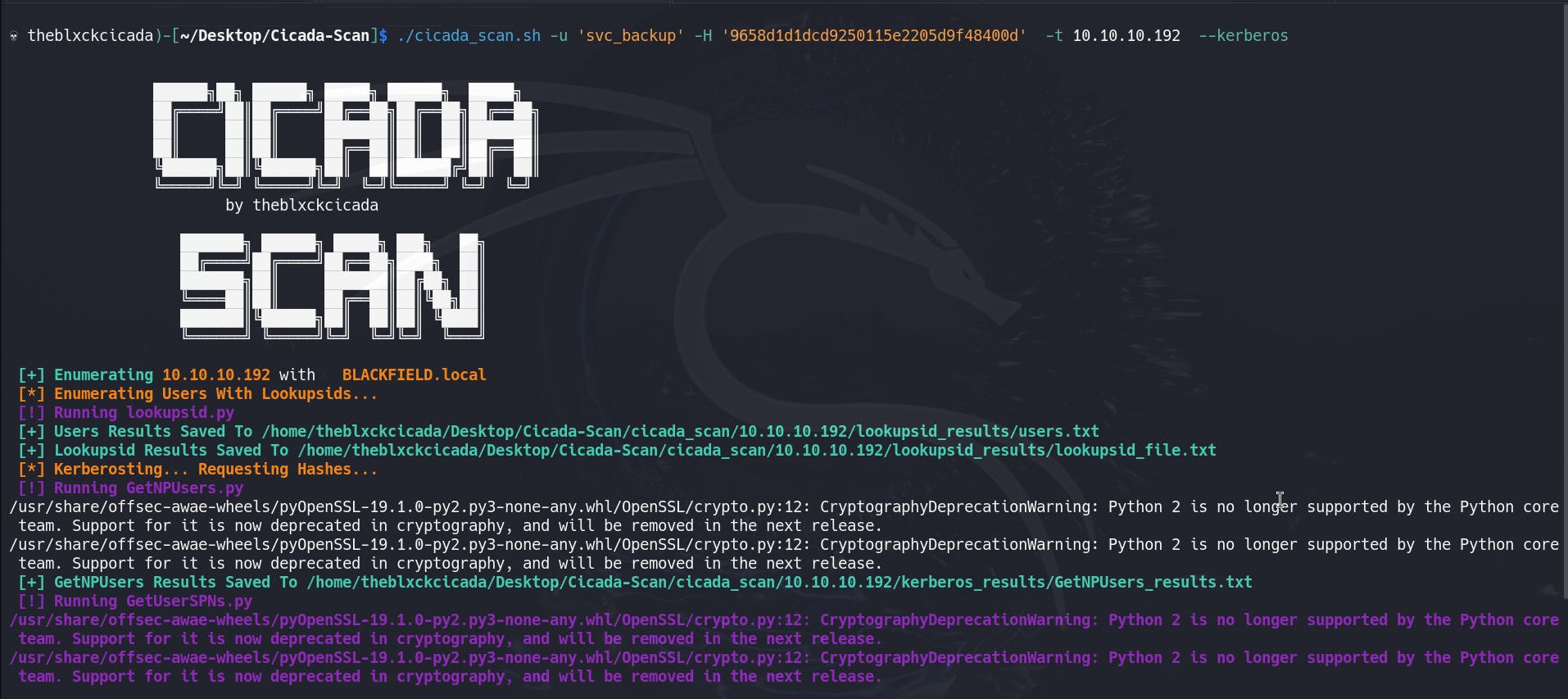
If you are unable to crack the NTLM hash that you found, don't worry, we can still help you. All you need to do is to inform the system that you possess a hash, instead of a password, and you will get the same outcomes as before.

There are many tools like Bloodhound, Kerberos, and WinRM. Below is an example of Kerberoasting.
I have provided you with the basic information to get started. If you want to explore this tool more, you can use the -h command to access the help menu. Please try it out and let me know what you think. Your feedback is valuable to me and will help me improve the tool.

